According to the auditing firm KPMG, the biggest obstacles for companies to rely on cloud solutions in 2019 were compliance with data protection and information security.(*1) Nevertheless, more and more companies are turning to the cloud, for example Amazon Web Services, or AWS for short. With a market share of 33% in 2019, AWS is the market leader among cloud providers.(*2) Customers of the cloud service include well-known and economically significant companies such as Siemens, Netflix, Philips, Zalando, the DB Group, but also banks such as the online bank N26.(*3) The use of cloud solutions also offers great advantages for smaller companies. There is no need to maintain their own data centers or servers, for example, which have to keep pace with constant technological change and thus incur investment costs. Billing is generally based on the pay-as-you-use principle, i.e. costs are only incurred for resources and services if they are actively used. These are generally lower than the provision, maintenance and support of own technical resources. Security and data protection play a prominent role at AWS. This is evidenced by the certificates awarded to AWS, which confirm compliance with data protection laws, depending on the location of the data center, and the standards in IT and information security. For the European region, these include the General Data Protection Regulation, the C5 standard, and the ISO standards 9001, 27001, 27017, and 27018.(*4)
Sensitive personal data security compliant in the AWS Cloud?
Allgemein, AWS Cloud, Digitale Kompetenz, OEV digital campus 360, Prototyping 18. Mai 2021
(*1) KPMG Cloud Monitor 2019
What is sensitive data or data requiring special protection?
Hover Box Element
The GDPR identifies personal data on ethnic and cultural origin, political, religious, and philosophical beliefs, health, sexuality, and trade union membership as particularly worthy of protection.
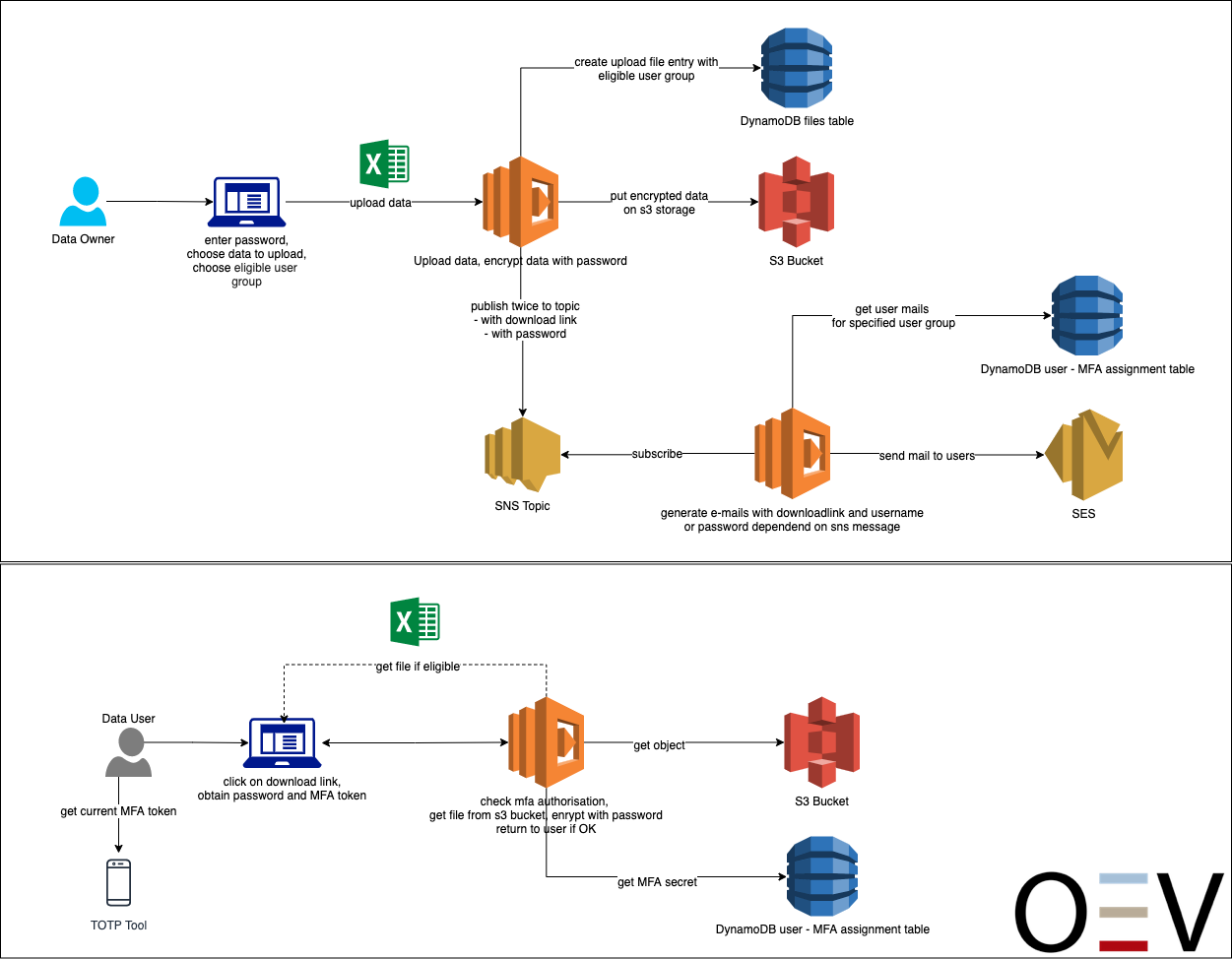
In a proof of concept, we showed how sensitive personal data can be stored securely and GDPR-compliant in a public cloud as part of an application. The goal was to develop an application in which files containing highly sensitive data can be made available within an organization and accessed by external employees.
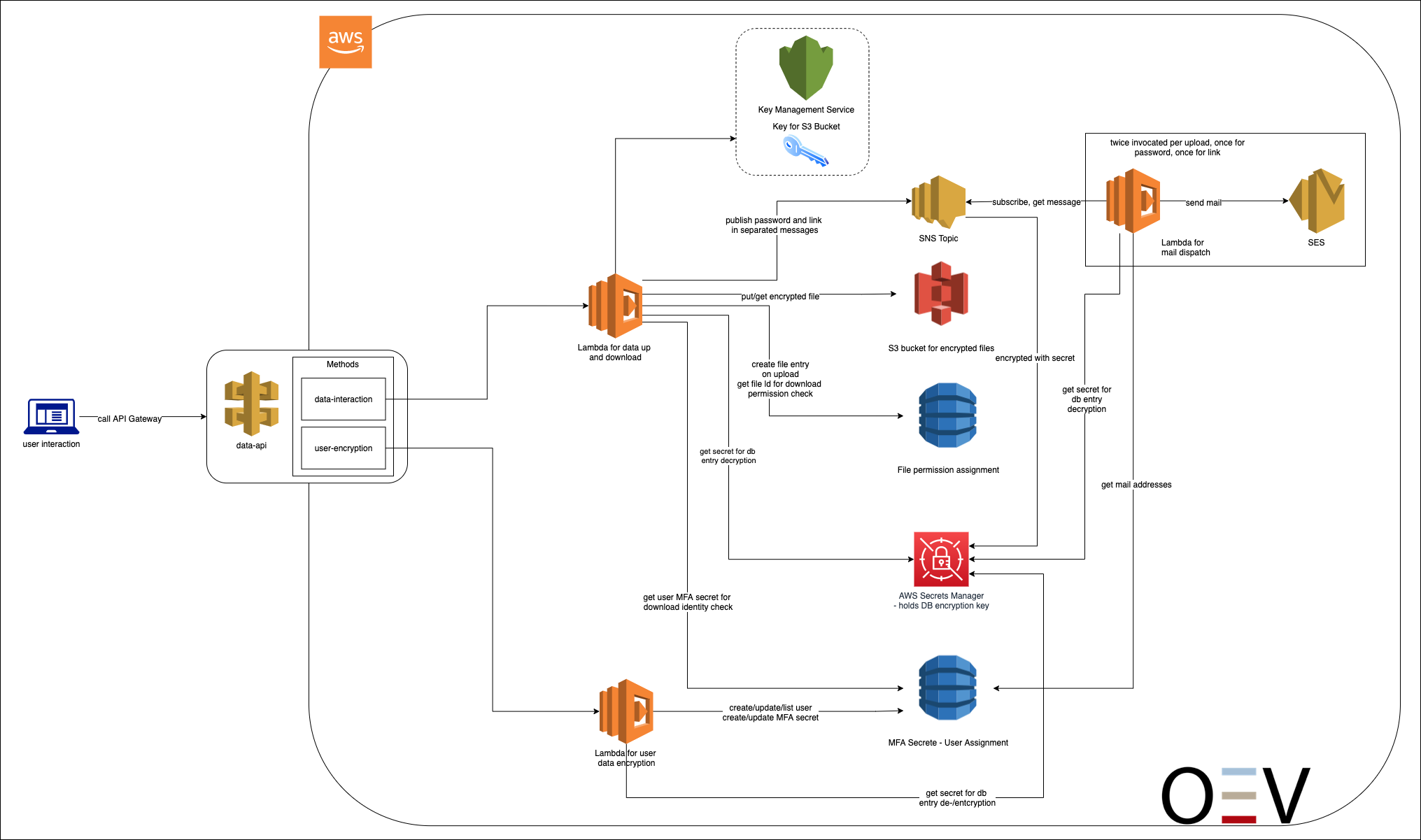
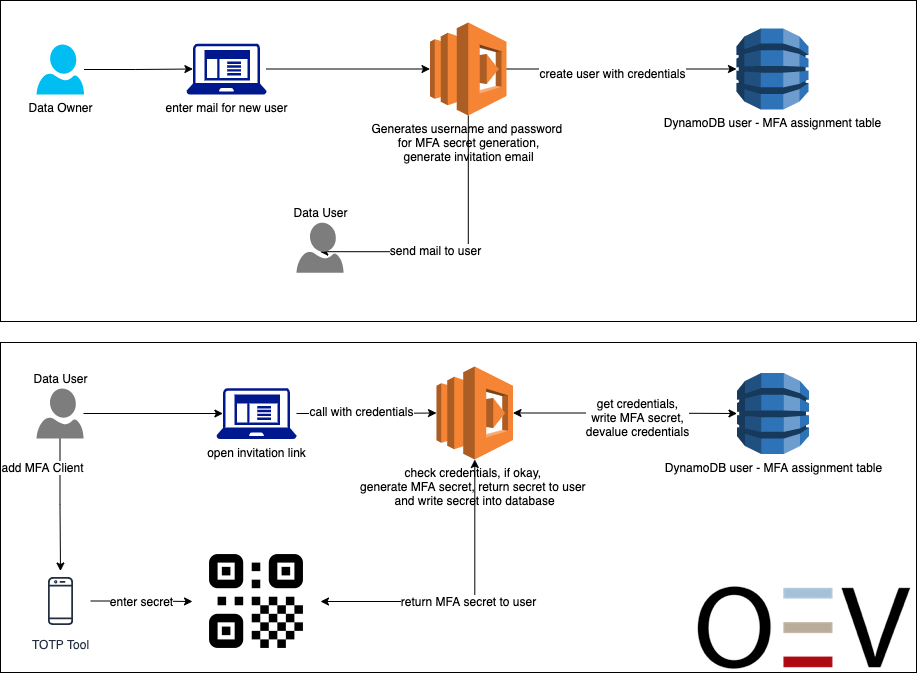
Basically, the application is built in a loosely coupled micro-services architecture and is thus based on Platform as a Service in the AWS Cloud. In addition to uploading files for provisioning, users should also be able to access them in the form of downloads. For this purpose, a user administration was implemented for the application, with which the access and download of files can be controlled individually for groups and users. Users are authorized via TOTP (Time-based One-time Password) multi-factor authentication and managed via an IP-restricted administration interface, so that changes to users can only be made by authorized persons within the company. The data is stored separately in two different tables in a database (Amazon Dynamo DB) and accessed based on the IAM (identity management) roles via an API interface through a Lambda function. The IAM used is AWS Identity and Access Management – the IAM service from AWS. There is end-to-end SSL encryption between the individual services. In addition, the data is encrypted using proprietary AES256-CBC security measures and the required passwords are stored hashed using a SHA512 algorithm. The API interfaces are provided by the AWS Api-Gateway service. This handles all tasks for accepting and managing connections as well as authorization, access control, monitoring and management of traffic. The service always provides an HTTPS encrypted interface. Accesses can be authorized with API keys, AWS IAM roles, and AWS Cognito. All processed data also resides in the runtime environment only at runtime; no persistent data is created within the runtime environment.
Process illustration
The AWS Secrets Manager is used to decrypt the data (user data and documents) from the database. The keys required for decryption are stored there. This key is requested dynamically for each decryption operation and is not stored in the runtime environment at any time. The database tables and the data they contain are encrypted separately. The AWS Key Management Service is used for hardware-side encryption of the database and the S3 bucket. This is an object storage service which provides high scalability, availability, security and performance. The service allows any amount of data to be stored and backed up. The stored objects are organized in a key-oriented manner. Authorization to use keys in both services is again done via the AWS IAM roles and permissions, thus a Principle of least Privilege strategy, such as required by BSI Grundschutz, can be implemented. Separating the encryption of database and user data also prevents administrators from unauthorizedly querying keys and decrypting and reading user data. The security policy of the S3 bucket is closed so that data can only be accessed via the S3 API with proper authorization. The data lists are stored as objects under a key in the bucket and are AES256-CBC encrypted byte streams.
What do all the abbreviations actually mean?
What is FIPS 140-2?
FIPS (Federal Information Processing Standard) 140-2 is a U.S. government standard that describes the encryption and related security requirements that IT products should meet for confidential but unclassified use.
What does FIPS 140-2 specify?
The standard ensures that a product employs sound security practices such as approved strong encryption algorithms and procedures. It also specifies how individuals or other processes must be authorized to use the product and how modules or components must be designed to interact securely with other systems.
Quelle: Seagate
What is AES?
The Advanced Encryption Standard (AES) is one of today’s standards for encrypting data. AES is a symmetric encryption method. This means that the same key is used for encryption and decryption (and must be known). AES uses a fixed block length of 128 bits and a defined key length of 128, 192 or 256 bits.
Basically, the longer the key or the number of bits, the more secure the data is encrypted and the more resources are required for encryption and decryption. The terms AES 128, AES 192 and AES 256 refer to the bit length of the key.
What is CBC?
Cipher Block Chaining Mode (CBC) is a kind of extension of basic encryption (AES) with feedback and some mathematical operations. So at the beginning of an encrypted session a cipher suite can be negotiated in which e.g. the encryption, the block size and the mode are defined.
In CBC mode, the plaintext block is XORed with the previous ciphertext block. This linkage makes each block directly dependent on the result of all previous blocks. This allows identical plaintext blocks to be encrypted to different ciphertext blocks, provided that at least one preceding block is different.
Quelle: Seagate
What does SHA mean?
SHA-2 (Secure Hash Algorithm) is the generic term for the cryptological hash functions SHA-224, SHA-256, SHA-384, SHA-512, SHA-512/224 and SHA-512/256, which were standardized by the U.S. National Institute of Standards and Technology (NIST) as the successor to SHA-1.
Quelle: Kryptowiki
Standards for information security
The individual standards for information security in the ISO 2700x series deal with diverse topics in the area of information security. For example, the international standard ISO 27001 specifies an information security management system (ISMS), ISO 27701 specifies a data protection management system, ISO 27017 provides guidance on information security measures for cloud computing, and ISO 27005 provides guidelines for information security risk management.
Quality management standards
ISO 9001 is the most widely used standard in quality management. It specifies the minimum requirements that must be implemented to meet customer requirements as well as other product or service quality requirements.
Quelle: DQS
To meet additional regulatory and compliance requirements, the AWS Key Management System is based on a fail-safe service where keys are stored on FIPS-140-2 validated hardware security modules. Every key usage is logged with Cloud-Trail and can be tracked.
A commissioned penetration test confirmed the security of the system architecture in that the intended attacks on the application did not succeed.
So we can conclude: Store sensitive personal data in the AWS Cloud in security- and law-compliant manner? Yes!

Nico Schönnagel

Alexander Röll
You have questions, suggestions or just want to chat with us? Let us know via the contact form and we’ll get back to you!